Sifflet Native App for Snowflake (private preview)
Install the Sifflet Native App to connect Sifflet to your Snowflake account
The Sifflet Native App for Snowflake is in private previewThis documentation page describes features that are not publicly released yet.
If you're interested in this deployment option, please contact your Customer Success Manager.
Overview
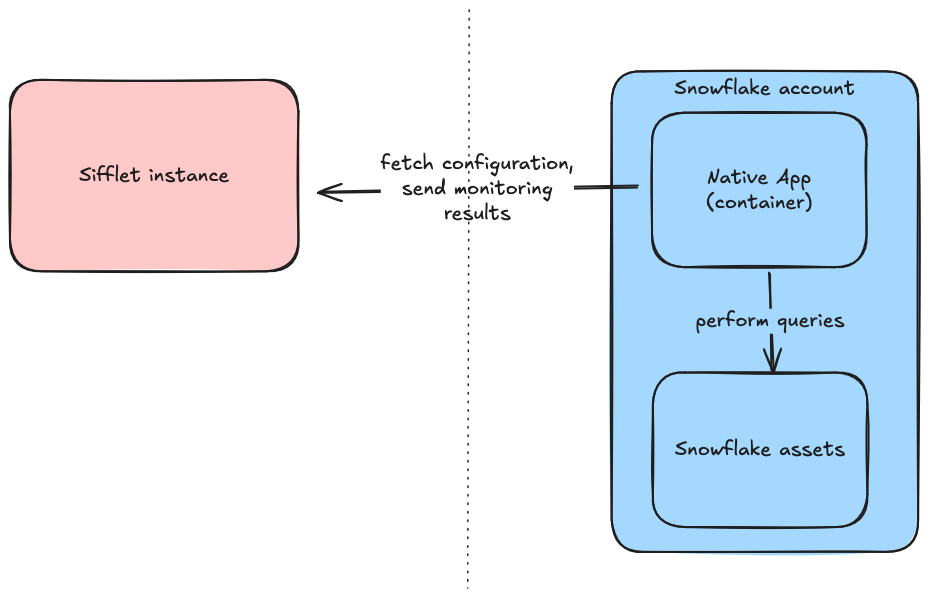
You can connect Sifflet to your Snowflake account using a Snowflake Native App. The benefits are:
- Stronger credentials security: you don't need to register any Snowflake credentials in Sifflet
- Compatible with stricter network policies: the Native App requires an explicit external access integration for egress traffic, and doesn't require opening any ingress traffic
- Improved auditability: the Native App logs all actions performed on your Snowflake account
If using the Native App, you can also procure Sifflet through the Snowflake Marketplace, using Snowflake credits. Contact your Account Executive for more information.
Installation
1. Create the Application in your Snowflake account
You can install the Snowflake Native App directly from the Snowflake Marketplace. During installation, you will be asked to enter the required information:
- your Sifflet tenant name (e.g if your sifflet URL is https://tenant.siffletdata.com, your tenant name is
tenant) - a Sifflet access token with the
Agent Service Accountrole. Follow this documentation to create the token: https://docs.siffletdata.com/docs/access-tokens. - a warehouse name. This will be the name of the warehouse that the Native App will create and use to query the Snowflake resources.
2. Grant privileges to databases to be discovered and monitored
You will need to give access to the Snowflake Native App to the resources you want to monitor through Sifflet. Run the following queries for every schema you want to see in Sifflet:
-- Set the value for native app name
set native_app_name = 'SIFFLET_NATIVE_APP_CHANGE_ME'; -- VALUE TO REPLACE with the name you used when installing the Snowflake native app
-- Read-only access to specific schemas
set database_name = 'DATABASE_CHANGE_ME'; -- VALUE TO REPLACE, database you want monitored
set schema_name = 'DATABASE_NAME.SCHEMA_NAME'; -- VALUE TO REPLACE
grant USAGE on database identifier($database_name) to application identifier($native_app_name);
grant USAGE on schema identifier($schema_name) to application identifier($native_app_name);
grant SELECT on all tables in schema identifier($schema_name) to application identifier($native_app_name);
grant SELECT on all external tables in schema identifier($schema_name) to application identifier($native_app_name);
grant SELECT on all views in schema identifier($schema_name) to application identifier($native_app_name);
grant SELECT on all streams in schema identifier($schema_name) to application identifier($native_app_name);
grant SELECT on all dynamic tables in schema identifier($schema_name) to application identifier($native_app_name);3. Create the Snowflake source in Sifflet
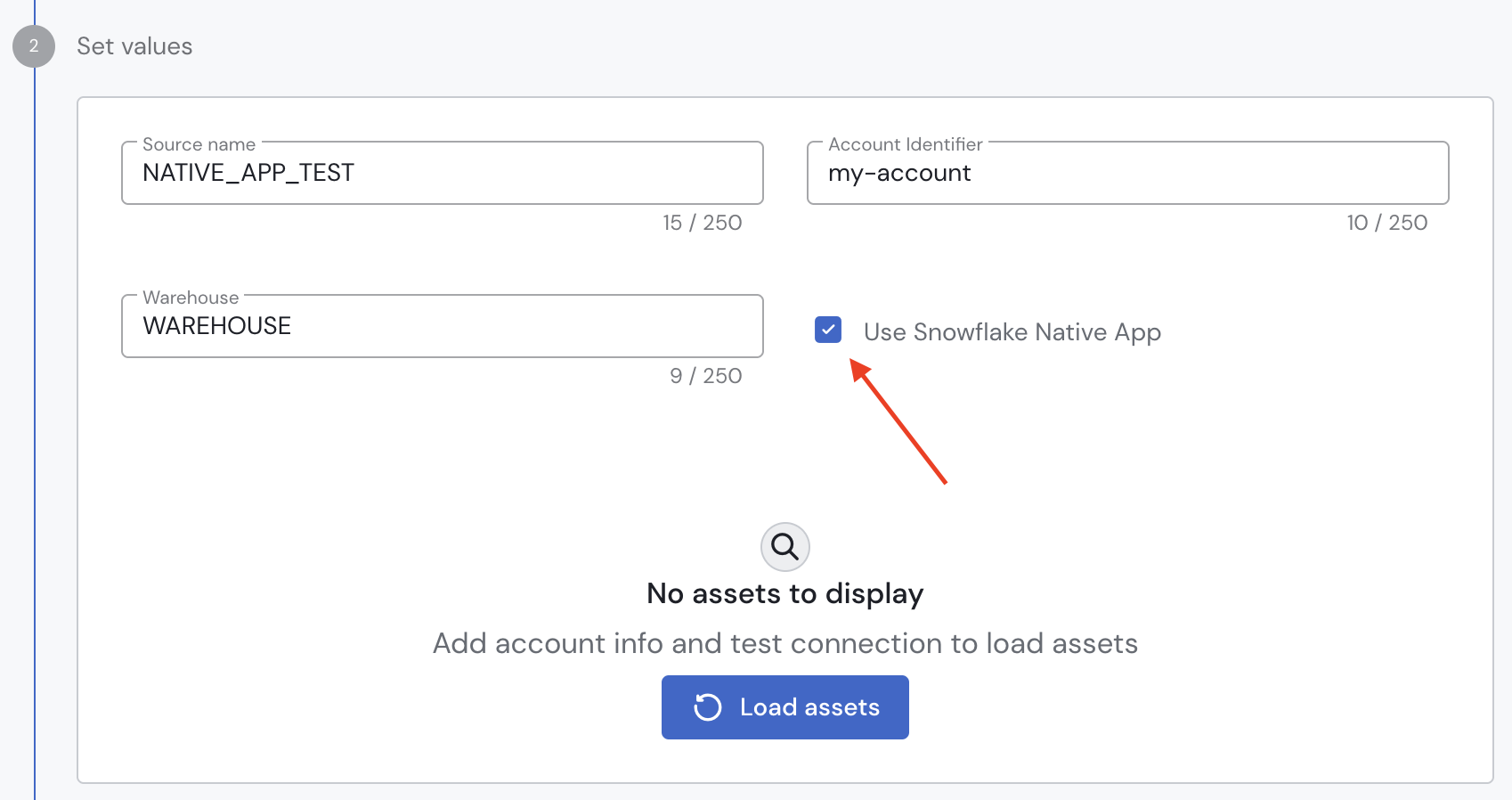
The last step is to create the Snowflake source in Sifflet. Follow this documentation to create the source: https://docs.siffletdata.com/docs/integration-management#adding-a-new-source.
Check the Use Snowflake Native App option to use the Native App. Note that when using the Sifflet Native App, you do not need to provide any credentials: the Snowflake OAuth Token provided to the container running the app will be used.
4. Create Sifflet Monitors to evaluate the quality of your assets
Once you've created your Snowflake source, this will create Assets in Sifflet's data catalog that you will be able to monitor. For this, you can create Sifflet Monitors that will query your assets through the Native App to evaluate their health, and potentially alert you when detecting an issue.
Security
Native App contents
The Native App creates the following objects:
- a single container, running a specialized version of the Sifflet Agent
- a Streamlit application to help you configure the Native App
- A table to record configuration data (the tenant name and warehouse name)
- Procedures to help with management of the Native App
Authentication and authorization
When installing the Native App, you will be asked for the following privileges:
BIND SERVICE ENDPOINT, which is necessary to create the Egress configuration to allow your App to contact your Sifflet instance.CREATE COMPUTE POOL, which allows the app to create a compute pool in which the Native App container will run.CREATE WAREHOUSE, which allows the app to create the warehouse it will use to run queries against the monitored Snowflake resources.IMPORTED PRIVILEGES ON SNOWFLAKE DB, which allows the app to query the Snowflake database to get information on tags, usage and costs.
After installing the Native App, you control which permissions you grant Sifflet on your Snowflake resources. As a baseline, Sifflet requires read-only access to all monitored assets. No write access is needed. These permissions are granted directly to the Native App as explained in Step 2 of the Installation process.
To authenticate the Native App against your Sifflet instance, you configure an access token through a Snowflake Secret that you create outside of the Native App context.
In the Native App, you specify an External Access Integration configured with the (unique) URL of your Sifflet instance. Thus, the Native App may never send information to another service nor to a different Sifflet customer.
Networking
The Native App doesn't expose any public endpoint. No ingress traffic network rule is necessary.
The Native App requires a single external integration. This external integration allows traffic from the Native App to your Sifflet instance. The Native App does not send any other egress traffic.
Further reading
Also see our dedicated security documentation: https://docs.siffletdata.com/docs/security.
Limitations
Because of limitations on the Snowflake Native App framework and on the Sifflet Native App implementation:
- It is not possible to grant
future grantsto an application. Because of this, discovery of new schemas in monitored tables is greatly limited and grants need to be explicitely given on all new schemas. - Lineage is not available through the Snowflake Native App.
Updated 4 months ago
