ForgeRock
RequirementsOnly users with the
Adminrole can enable SSO in Sifflet.
To set up the SSO in ForgeRock, please go through the following steps:
- Configure your Identity Provider (IdP)
- Configure the SSO in Sifflet
- Test your SSO
1- Configure Your Identity Provider (IdP)
The below steps describe the different steps required to configure ForgeRock with a basic set-up, more details can be found on ForgeRock documentation.
a. Retrieve the SSO Details in Sifflet
- Log in to Sifflet
- In
Settings>SSO: click the toggle button to turn SSO on - Choose the
Otherplatform - Copy the information that shows up under
Sifflet Configuration, you will need it in the next section.
b. Create a Hosted IdP Entity Provider (optional)
- Log in to ForgeRock
- Create an IDP Entity provider by going to
Applications_>Federation>Entity Providers>Add Entity Provider>HostedEntity ID: For instanceMainEntityEntity Provider Base URL: Do not change itIdentity Provider Meta Alias: For instanceMainIDP- Click
Create
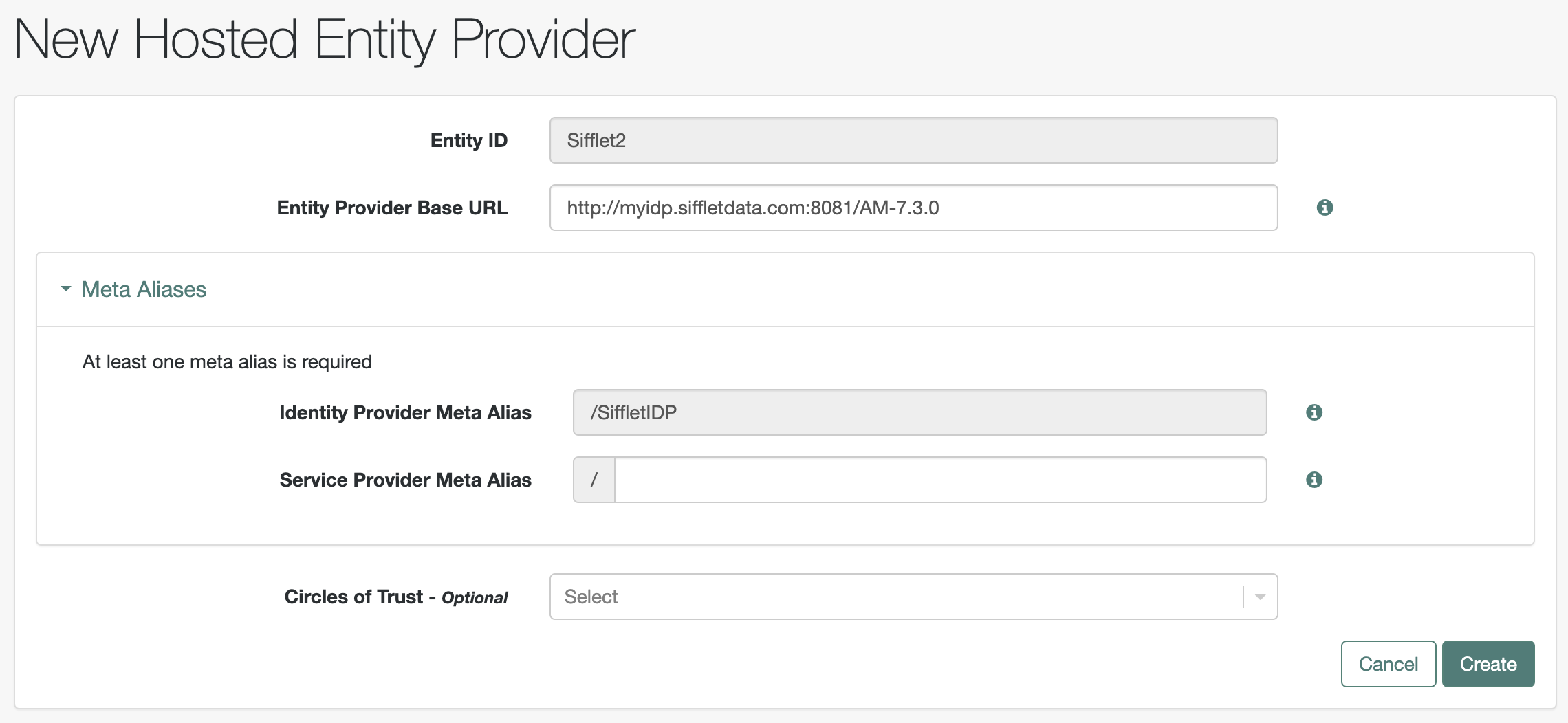
Creating a Hosted Entity Provider
c. Check NameID Format and Mapping
Ensure that one of the following NameID formats is supported and mapped to the email:
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddressurn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
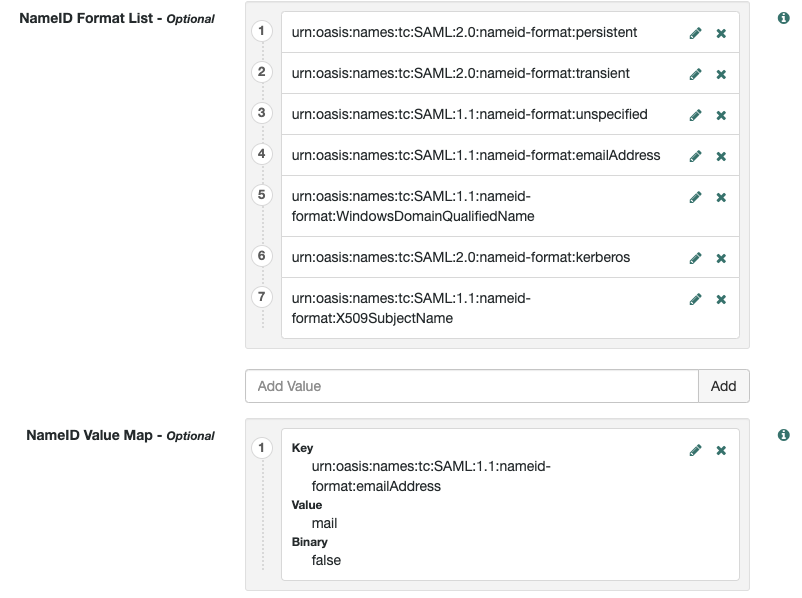
Checking Name ID Format and Mapping
d. Create a Remote SP Entity Provider
- Create a SP Entity provider by going to
Applications>Federation>Entity Providers>Add Entity Provider>Remote - Create an XML file from the below template, where you replace:
{{EntityID}}by the value of theAudience Restrictionfield in Sifflet{{AssertionConsumerServiceLocation}}by value of theSingle Sign On URLfield in Sifflet
<?xml version="1.0" encoding="UTF-8"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="{{EntityID}}">
<md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="{{AssertionConsumerServiceLocation}}" index="1"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>- Back in ForgeRock import the XML file you just created
- Click
Create
d. Create a Circle of Trust (optional)
- Create a Circle of Trust by going to
Applications>Federation>Circles of Trust>Add Circle of TrustName: For instanceSiffletCoT- Click
Create - In Entity Providers, add the name of the two Entity Providers you just created. For instance:
MainEntity|saml2andhttp://localhost:8090/saml2/service-provider-metadata/saml2|saml2 - Click
Save Changes
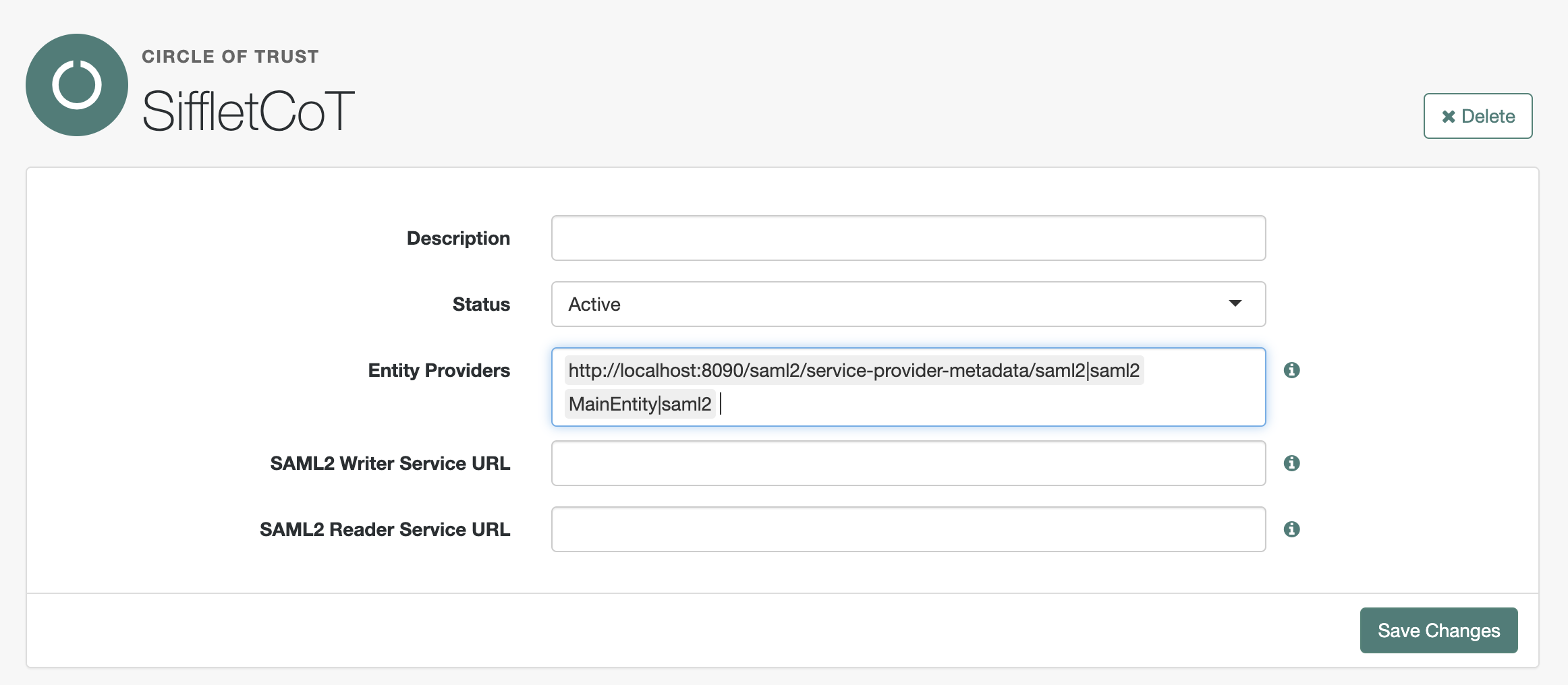
Creating a Circle of Trust
2- Configure the SSO in Sifflet
- Download the metadata for the IDP Entity Provider you created above (suggested name was
MainEntity) by going to{ForgerockBaseURL}/saml2/jsp/exportmetadata.jsp?entityid={EntityName}&realm={Realm}where{ForgerockBaseURL},{EntityName}and{Realm}should be replaced with the appropriate values. - Update Sifflet SSO configuration with:
Identity Provider Single Sign-On URL: The content of theLocationattribute for the property<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location=”THIS VALUE” />.Identity Provider Entity ID: The content of theentityIdattribute at the root.Signing X.509 Certificate: the content of the<X509Certificate>property that is in the<KeyDescriptor use="signing">section. Don’t forget to add the following lines before and after the content:- To add before:
-----BEGIN CERTIFICATE----- - To add after:
-----END CERTIFICATE-----
- To add before:
3- Test Your SSO
- You can now test your SSO by pressing the
Testbutton on the bottom right of the page
- If successful, don't forget to press the
Savebutton to effectively activate the SSO.

The configuration is done !
On your next login, you will see the following login screen:

Troubleshooting
In ForgeRock Access Audit logs: Identity Provider ID is null
This error is usually caused by an incorrect Identity Provider Single Sign-On URL in Sifflet configuration. It should look like {ForgerockBaseUrl)/SSOPOST/metaAlias/{IDPMetaAlias}.
In ForgeRock Access Audit logs: Error retrieving meta data.
Make sure the you create the right role for the entity provider (IDP vs SP role).
In Sifflet UI: {"title":"Unauthorized","status":401,"detail":"Full authentication is required to access this resource"}
Check the X509 Certificate is correctly configured in Sifflet and it is the right one (should correspond to the signing KeyDescriptor, not the encryption.
Also verify that you’ve added the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----.
The full value should look like:
-----BEGIN CERTIFICATE-----
MIIDdzCCA.....s009kbW6inN8zA6
-----END CERTIFICATE-----In ForgeRock Access Audit logs: The SAML Request is invalid.
Verify that the Circle of Trust is correctly configured. It should contain the two entity providers.
In ForgeRock Access Audit logs: Unable to do Single Sign On or Federation. (Permission denied on setting attributes for amAdmin.)
You may already be connected with the amAdmin account. Disconnect and then try again.
In Sifflet UI: Authentication succeeded, but you need to use an account email matching an existing Sifflet Admin login
This error means that the Name ID assertion in the SAML response token is not found among the Sifflet user admins.
This can have multiple causes.
- The user does not exist among Sifflet users
Add manually the user with the right email address in the Sifflet users. - The user is not an admin
The user exists but is not an admin (update the user as an admin). - The Name ID assertion in the SAML response is not an email address
In the IDP application (service entity), make sure the right Name ID format is used and email address is correctly mapped.
In ForgeRock Access Audit logs: Unable to do Single Sign On or Federation. (Unable to generate NameID value.)
In the IDP service entity, make sure the right Name ID format is used.
In ForgeRock Access Audit logs: Unable to do Single Sign On or Federation. (The Assertion Consumer Service URL … is not registered in the metadata for the SP …)
If you create the service provider as Hosted entity provider, make sure you have updated the Assertion Consumer Service configuration section.
Updated 4 months ago
