Other
RequirementsOnly users with the
Adminrole can enable SSO in Sifflet.
To set up the SSO with your IdP, please go through the following steps:
- Configure your Identity Provider (IdP)
- Configure the SSO in Sifflet
- Test your SSO
1- Configure your Identity Provider
a. Retrieve the SSO Details in Sifflet
- Log in to Sifflet
- In
Settings>SSO: click the toggle button to turn SSO on - Choose the
Otherplatform - Copy the information that shows up under
Sifflet Configuration, you will need it in the next section.
b. Configure Sifflet as a Service Provider in your Identity Provider
- Log in to your IdP
- Refer to your IdP's documentation for specific instructions on how to add a service provider to your IdP and add the content from the
Audience RestrictionandSingle Sign On URLfields in Sifflet to your IdP service provider definition.
If you need to upload a metadata file on your IdP, you can create an XML file from the below template, where you replace:
{{EntityID}}by the value of theAudience Restrictionfield in Sifflet{{AssertionConsumerServiceLocation}}by value of theSingle Sign On URLfield in Sifflet
<?xml version="1.0" encoding="UTF-8"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="{{EntityID}}">
<md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="{{AssertionConsumerServiceLocation}}" index="1"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>- Ensure that one of the following NameID formats is supported and mapped to the email:
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddressurn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
2- Configure the SSO in Sifflet
- Get the metadata from your IdP
- Update Sifflet SSO configuration with
Identity Provider Single Sign-On URL: The content of theLocationattribute for the property<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="THIS VALUE" />Identity Provider Entity ID: The content of theentityIdattribute at the root.Signing X.509 Certificate:The content of the<X509Certificate>property that is in the<KeyDescriptor use="signing">section.Don’t forget to add the following lines before and after the content:- To add before:
-----BEGIN CERTIFICATE----- - To add after:
-----END CERTIFICATE-----
- To add before:
3- Test your SSO
- You can now test your SSO by pressing the
Testbutton on the bottom right of the page
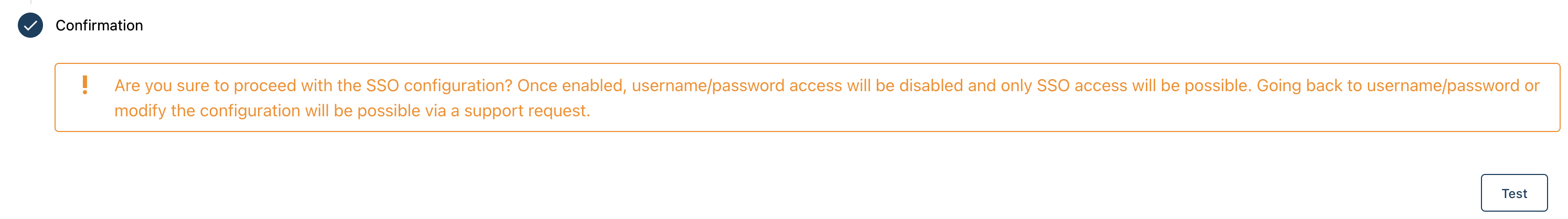
- If successful, don't forget to press
Saveto effectively activate the SSO.

The configuration is done !
On your next login, you will see the following login screen:

Tested IdPs and Tools
In addition to Okta, Google, Azure Active Directory, and Forgerock, the following IdPs and tools were successfully tested by the Sifflet team:
- BoxyHQ
Updated 3 months ago
